We take your tangled mountain of cables and make an organized cable system that is easy to service, upgrade and…
A new report indicates that attackers are increasingly targeting Linux machines as the operating system becomes increasingly popular among enterprise users.
The basics to creating a secure home or small business WIFI network, you need to start by securing your Wi-Fi…
Virus writers belong to one of four broad groups: cyber-vandals, who can be divided into two categories, and more serious…
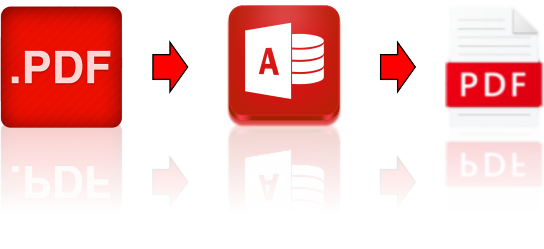
I had a requirement to maintain information in PDF forms provided by a third party, but my choices were either to manually fill each one individually with a pen or to fill each one in a browser while copy/pasting all the information from another application (Microsoft Access). Neither of those solutions seemed very productive or had any way of catching input errors until I wrote this solution.
A little over a year ago, Microsoft announced their intention to rebuild Microsoft Edge on the Chromium open-source project, focusing…